Showing 1 to 15 of 2075 results


TWISCO – Digital TWIn for Sustainable Supply Chain in Construction
Innovative Products and Technologies Luxembourg Institute of Science and Technology (LIST)

Novel luminescent probes of lanthanide complexes for sensing of biomolecules
Patents for licensing Consejo Superior de Investigaciones Científicas

Vibration-assisted ball burnishing: A solution for Surface enhancement through acoustoplasticity
Innovative Products and Technologies UPC

Method for predicting sex in fish
Patents for licensing CSIC - Consejo Superior de Investigaciones Científicas

Planting container facilitating the storing and planting of seeds, bulbs or tubers in difficult conditions.
Innovative Products and Technologies Luxembourg Institute of Science and Technology (LIST)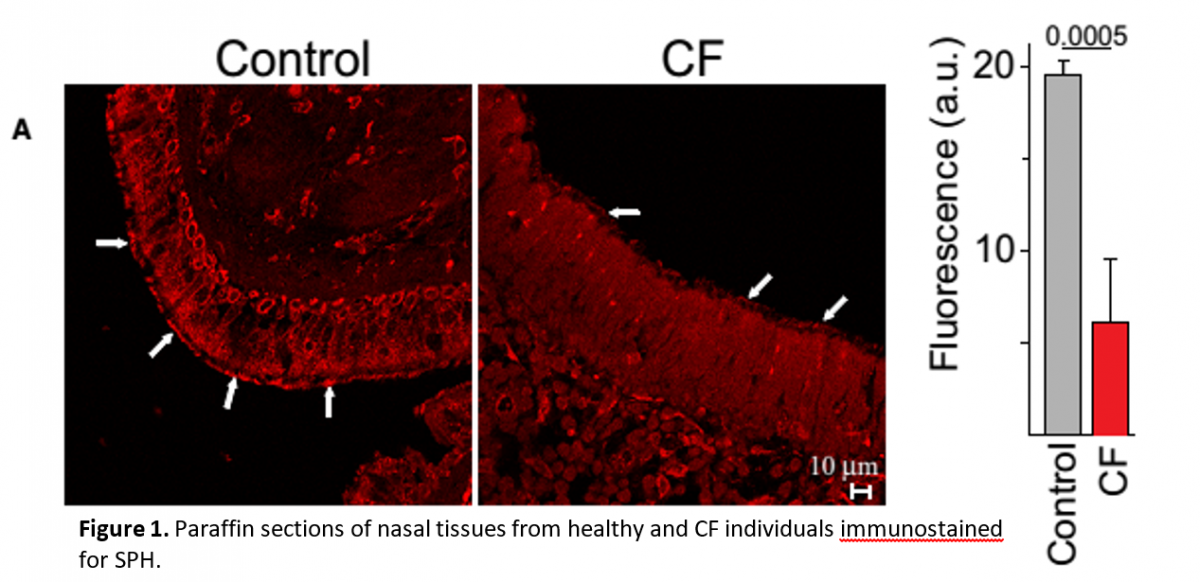

Preventing Infections Using Lipid Based Molecules
Patents for licensing Yeda

Effective natural stimulants for plants
Innovative Products and Technologies Yury Savinykh

Preventing Biofilm Formation by Enzyme Inhibitors
Patents for licensing Yeda

Retractable hood for motorized wheelchairs.
Patents for licensing UNIVERSIDAD DE BURGOS

Direct sensor for electron microscopy with in-pixel energy measurement
Patents for licensing Consejo Superior de Investigaciones Científicas![Waterproof optical probe with continuous and automatic register for nitrate concentration control of water resources (superficial […]](https://static3.innoget.com/uploads/5349c640059153b0be7eea79b37c7bc5166cdc76.jpg)

Waterproof optical probe with continuous and automatic register for nitrate concentration control of water resources (superficial […]
Patents for licensing Universidad de Alcalá-OTRI

Augmented Reality on Android: Arquiz
Patents for licensing UNIVERSIDAD DE BURGOS

Observatory for Climate, Environment and Biodiversity
Research Services and Capabilities Luxembourg Institute of Science and Technology (LIST)

Multilevel Active-Clamped Electrical Energy Converter
Patents for licensing Universitat Politècnica de Catalunya - UPC

